Concepts
Quantum Key Distribution (QKD)
An overview of cryptography
The Concise Oxford English Dictionary defines cryptography as “the art of writing or solving codes.” This is historically accurate, but does not capture the current breadth of the field or its present-day scientific foundations. Cryptography has been an essential part of our everyday life and the importance of it is increasing with each passing day. Be it an online bank transaction, or a chat session in social media, or anything else online, we want our data to be secure from malicious activities. Even the security of a nation is also dependent on the security of strategic information. Modern day cryptography can be defined as the “study of mathematical techniques for securing digital information, systems, and distributed computations against adversarial attacks.” The modern cryptographic schemes have been enabling us to be secured in today’s digital life. But we are in a brink of change!
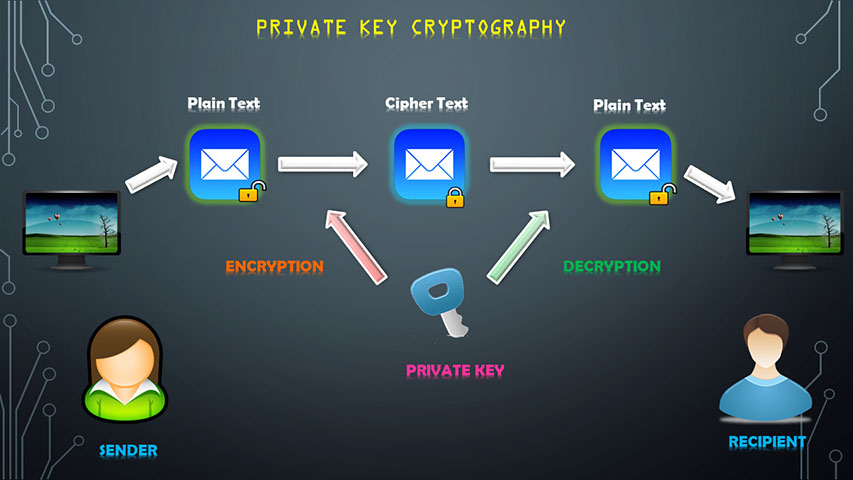
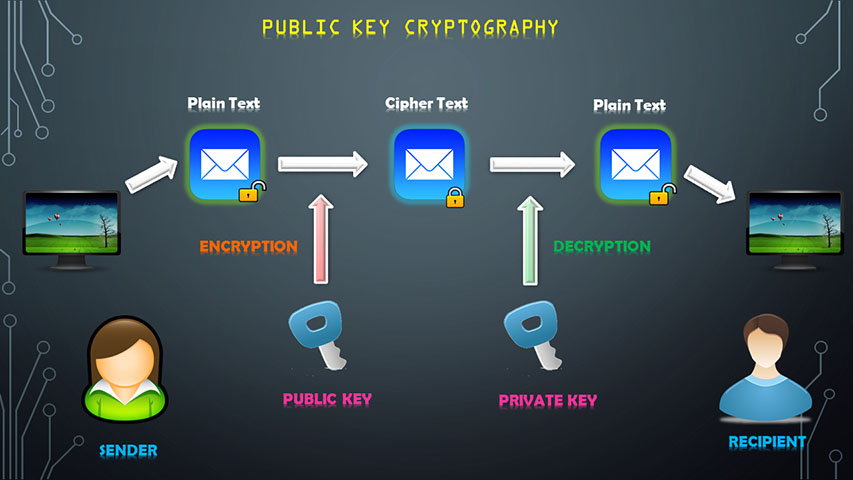
Modern cryptography can be largely classified into two main forms – the private key cryptography and the public key cryptography. In the former, same key is used for encryption (locking) as well as decryption(unlocking) of the message i.e. the sender and the receiver of the message must hold the same key whereas, as the name itself suggests, the sender encrypts the message with the public key while the receiver decrypts the message with the private(secret) key, in the latter. Thus, in a public key cryptographic scheme, anyone will be able to send an encrypted message but the intended recipient will be the only one to be able to decrypt it.
Why we need Quantum Key Distribution (QKD)
While we have been comfortably using modern cryptographic schemes, they have some drawbacks too. The security of private key cryptography depends on the length of the key. Larger the key space, more secure is the scheme. With increase in computational power of Classical computers as well as anticipation of application of more efficient quantum search algorithms (ex-Grover’s algorithm), the resource oriented problem of secure key distribution has come up. On the other hand, the security of public key cryptography depends on the complexity of the mathematical theories they are based and hence, they are vulnerable to efficient algorithms. For ex- Shor’s algorithm can perform factorization in polynomial time which makes the security of RSA cryptosystem vulnerable. With the impending dawn of quantum computation, the public key cryptographic schemes might soon cease to be staying unbreakable. Thus, private key cryptosystems with longer key length can be the solution if the key distribution schemes can be made secure and efficient, which is where QKD comes into play.
What is Quantum Key Distribution
Quantum key distribution is a cryptographic technique which allows two remote users to establish a secure key (random bit string) between them which can be used further for secure communication, using the principles of quantum mechanics. Stephen Wiesner, in his paper titled “Conjugate coding” (1970), provided the very first idea of quantum cryptography. In 1984, Charles Bennett and Giles Brassard put forward the first quantum cryptography protocol named as BB84 protocol which uses polarisation states of photon as the physical entity to generate a secure bit string among two users In 1991, Arthur Ekert invented the E91 protocol which first used quantum entanglement for QKD, followed by the BBM92 protocol. The most important advantage of QKD is that, in principle, the users can detect the presence of an eavesdropper who is trying to gain information from the transmission of information occurring between the sender and the receiver. If the eavesdropping level is below a certain threshold, a key can be established which is guaranteed to be secured. The most important features of quantum mechanics which are used are
- Hiesenberg’s uncertainty principle which puts a fundamental limit to the knowledge an observed might have of a quantum system.
- No-cloning theorem which states any arbitrary quantum state cannot be copied to generate replicas.
- Quantum Entanglement which creates a non-classical correlation between two quantum entities.
We can get further insight about these features in the perspective of a QKD protocol.
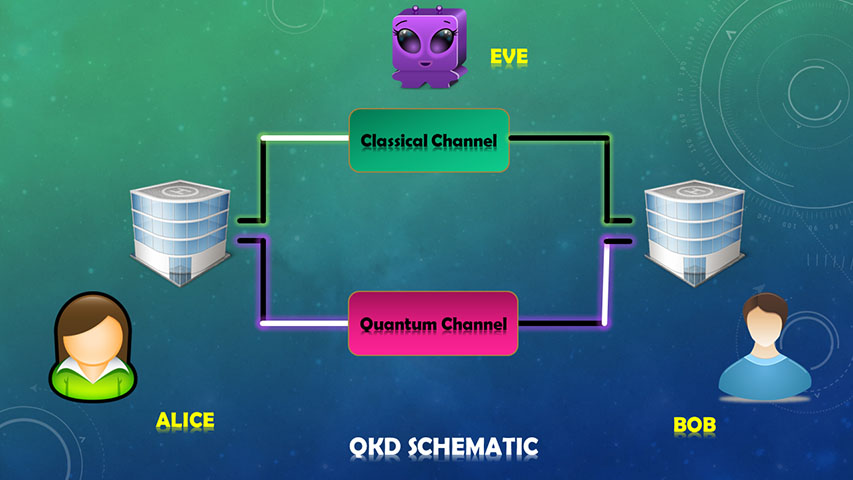
Meet Alice, Bob and Eve
Alice and Bob are the users of a QKD protocol who want to generate a secure key between them for secret communication. They are assumed to work on impenetrable labs and have full control over their devices. Alice and Bob both have random number generators. They have access to an authenticated quantum communication channel through which they will send and receive quantum states and an authenticated classical channel for any communication required for the protocol.
Eve is the malicious person who wants to eavesdrop and gain information. Eve knows the protocol being used except for any random number the protocol might ask Alice and Bob to produce. Eve is all powerful, in other words i.e. Eve has a quantum computer with arbitrary quantum memory. Eve sees a perfect quantum channel i.e. any noise in the channel can be attributed to the work of the eavesdropper. Thus any error in the generated key string will be considered to have happened because of the eavesdropper.
The BB84 protocol
The BB84 protocol uses the polarization state of photons to encode key bits. A pair of orthonormal polarization bases are required because according to the Heisenberg's principle if the polarization state is defined in one of the basis, it is undefined in the other. The protocol uses such four polarization states. The no-cloning theorem make sure that the malicious eavesdropper cannot hack into the channel and the copy the transmitted quantum states. Thus, any disturbance created by Eve can be detected by Alice and Bob. Alice randomly prepares photons in one of the four polarisation states – horizontal (H) and vertical (V) defined in the rectilinear basis, diagonal (+) and anti-diagonal (-) in the diagonal basis and sends it to Bob over the quantum communication channel. ‘H’ and ‘+’ polarisation states corresponds to binary “0” whereas ‘V’ and ‘-’ polarisation states corresponds to binary “1”. Both Alice and Bob must agree upon the convention beforehand. Bob randomly selects a basis (Rectilinear (R) or Diagonal (D)) and measures the polarisation of the incoming photon. After the completion of the transmission of the desired number of quantum states, Alice and Bob publicly discusses the basis of preparation and measurement they have chosen for each state and keeps only those bits in which their bases matched. This process is called sifting and if there is no eavesdropping, this will result in the generation of an identical bit string (known as the sifted key) shared by the two users. Whereas, any eavesdropping will produce error in the sifted key which can be detected. Alice and Bob publicly announce a part of the sifted key and calculates the error. The error in the sifted key is known as the quantum bit error rate (QBER) and if it is below a certain threshold, Alice and Bob considers the key to be secured or and else, the protocol is aborted. For BB84 protocol, the threshold value of the QBER is 25%. The following table tries to capture the aforementioned concept.
